When the Alarms Blare: Navigating the Storm of Data Breaches and Security Threats with Effective Incident Response
In the digital age, where data breaches and security threats lurk like unseen storms, preparedness is your most potent weapon. Just as ships have emergency response plans for rough seas, organizations need robust incident response (IR) strategies to weather the tempests of cyberattacks. So, intrepid captains of digital vessels, gather your crew, equip yourselves with knowledge, and chart a course through the murky waters of incident response – for a swift and effective navigation can mean the difference between a minor scare and a digital disaster.
Why Effective Incident Response Matters for security threats:
Minimized Damage:
Prompt and effective response can contain the breach, limit data loss, and prevent further damage to your systems and reputation.
Swifter Recovery:
A well-defined IR plan helps you recover quickly, minimizing downtime and business disruption.
Reduced Costs:
Early detection and containment can significantly reduce the financial impact of a breach.
Compliance Assurance:
Many data privacy regulations mandate specific breach notification and response procedures, making effective IR essential for legal compliance.
Strengthened Security Posture:
Learning from each incident allows you to improve your defenses and prevent future attacks.

Stats Paint a Worrying Picture:
- 43% of data breaches involve human error. (Verizon, 2023 Data Breach Investigations Report)
- The average cost of a data breach is $4.24 million. (IBM Security, 2023)
- Only 66% of organizations have a formal incident response plan. (Ponemon Institute, 2023)
- 72% of businesses experience at least one phishing attack every month. (Verizon, 2023 Data Breach Investigations Report)
From Panicked Scrambling to Calm Control: Building Your IR Arsenal
Establish an Incident Response Team (IRT):
Assemble a dedicated team with specialized skills and clear roles and responsibilities for each stage of the response process.
Craft a Comprehensive IR Plan:
Develop a documented plan outlining detection, containment, eradication, recovery, and post-incident review procedures.
Identify and Prioritize Assets:
Classify your data and systems based on criticality to prioritize response efforts and protect the most sensitive information. safegaurd from “Security Threats”
Invest in Incident Response Tools:
Utilize technologies like Security Information and Event Management (SIEM) systems and forensics tools to facilitate detection, investigation, and evidence collection.
Conduct Regular Testing and Drills:
Practice your IR plan through tabletop exercises and simulations to identify weaknesses and refine your response procedures.
Recommended Tools and Techniques:
Security Information and Event Management (SIEM) Systems:
Tools like Splunk and LogRhythm aggregate security data from diverse sources, providing real-time insights and threat detection capabilities.
Digital Forensics and Incident Response (DFIR) Tools:
Solutions like Mandiant and FireEye offer advanced capabilities for incident investigation, evidence collection, and analysis.
Threat Intelligence Platforms:
Tools like Palo Alto Networks Cortex XSOAR and ThreatStream provide insights into emerging threats and vulnerabilities, assisting in proactive defenses.
Communication and Collaboration Platforms:
Tools like Slack and Microsoft Teams facilitate real-time communication and collaboration among IR team members and stakeholders.
Incident Response Playbooks:
Pre-defined playbooks for various incident scenarios can guide your response team and ensure consistent, efficient action.
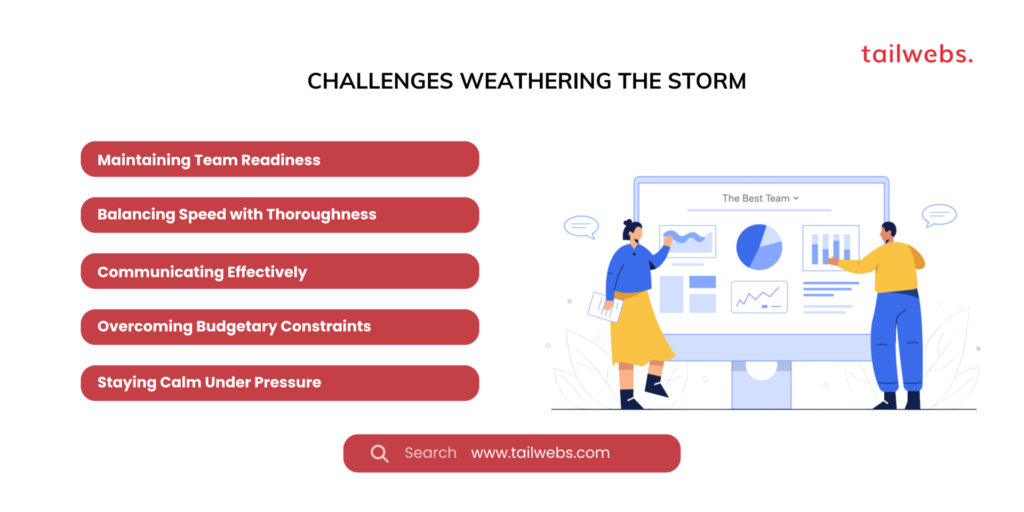
Challenges Weathering the Storm:
Maintaining Team Readiness:
Keeping your IRT skilled and trained amidst ever-evolving threats requires ongoing training and knowledge updates. safegaurd from “Security Threats”
Balancing Speed with Thoroughness:
Acting quickly is crucial, but rushing investigations can lead to overlooking critical evidence or implementing remediation measures prematurely.
Communicating Effectively:
Balancing transparency with legal and privacy concerns while managing stakeholder expectations requires clear and concise communication throughout the incident response process.
Overcoming Budgetary Constraints:
Investing in IR tools, training, and personnel can be costly, making it crucial to demonstrate the value of a robust IR program to secure necessary resources.
Staying Calm Under Pressure:
High-pressure situations can lead to panicked decision-making. Regular drills and a well-defined communication plan can help maintain composure and ensure clear-headed response.
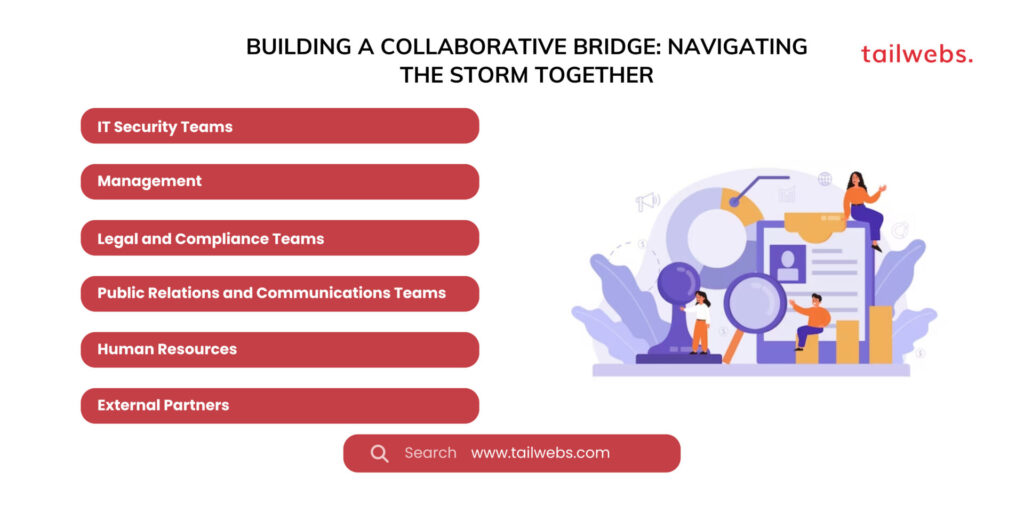
Building a Collaborative Bridge: Navigating the Storm Together
Conquering these challenges demands a united front:
IT Security Teams:
Lead the incident response process, activate the IR plan, and utilize technical expertise for containment and eradication.
Management:
Provide leadership, decision-making support, and resource allocation throughout the response and recovery process.
Legal and Compliance Teams:
Advise on legal requirements, data privacy regulations, and communication strategies to ensure compliance and mitigate legal risks.
Public Relations and Communications Teams:
Craft clear and consistent messages for stakeholders, minimizing reputational damage and maintaining public trust.
Human Resources:
Address employee concerns, manage internal communications, and provide support to impacted individuals.
External Partners:
Leverage the expertise of incident response consultants, forensics investigators, and legal counsel for specialized assistance when needed.
By working together and harnessing the power of collaboration, even small organizations can weather the storm of a data breach.
Here are some additional tips to ensure your collaborative response becomes a beacon of resilience:
Conduct Regular Post-Incident Reviews:
Analyze each incident to identify root causes, learn valuable lessons, and improve your IR plan and security posture.
Foster a Culture of Security Awareness:
Educate employees on cybersecurity best practices, phishing scams, and their role in reporting suspicious activity.
Practice Continuous Improvement:
Regularly update your IR plan, tools, and training to adapt to evolving threats and industry best practices.
Share Knowledge and Insights:
Participate in industry forums and communities to share learnings and collaborate on improving collective cyber defenses.
Celebrate Successes and Resilience:
Recognize the efforts of your IR team and stakeholders in successfully navigating through a challenging incident.
Remember, incident response is not a reactive measure; it’s an ongoing process of preparation, collaboration, and continuous improvement. By building a robust IR program, equipping your team with the necessary tools and knowledge, and fostering a culture of security awareness, you can transform your organization into a resilient vessel, capable of weathering even the most turbulent storms in the ever-changing digital landscape. So, raise the sails of preparedness, assemble your crew of skilled responders, and embark on the noble quest to navigate the choppy waters of cyber threats with confidence and control. Together, you can ensure the safety of your digital harbor and emerge stronger from any storm that may come your way.