In today’s digitally driven world, software is the backbone of countless businesses. For IT firms, building secure and scalable software is paramount for client satisfaction and long-term success. Secure software safeguards sensitive data and protects against cyberattacks, while scalable software adapts to accommodate growth and evolving user demands. This comprehensive guide explores best practices for IT firms to build secure and scalable software solutions, empowering them to deliver exceptional value to their clients.
The Cost of Insecurity: Why Secure Software Development Matters
Data breaches are on the rise, costing businesses billions of dollars annually. According to the IBM Cost of a Data Breach Report 2023: https://www.ibm.com/reports/data-breach, the global average cost of a data breach in 2023 reached a staggering $4.35 million. These breaches not only result in financial losses but also damage brand reputation and erode customer trust.
Building Secure Software: A Proactive Approach
Here are key practices for IT firms to develop secure software:
Security by Design:
Integrate security considerations throughout the entire software development lifecycle (SDLC). This includes threat modeling, secure coding practices, and vulnerability assessments.
Secure Coding Practices:
Developers should adhere to secure coding guidelines established by organizations like OWASP (Open Web Application Security Project) to mitigate common vulnerabilities like SQL injection and cross-site scripting (XSS).
Regular Penetration Testing:
Enlist security professionals to conduct penetration testing to identify and address potential vulnerabilities in the software before deployment.
Data Encryption:
Encrypt sensitive data at rest and in transit to safeguard it from unauthorized access.
Access Control & Authentication:
Implement robust access control mechanisms to ensure only authorized users can access specific data and functionalities within the software.
Secure Coding Training:
Invest in ongoing security awareness training for developers to equip them with the knowledge and skills to write secure code.
Scalability: Building Software That Grows with Your Clients
Scalability allows software to handle increasing user loads, data volumes, and functionality requirements without compromising performance. Here’s how IT firms can ensure software scalability:
Identify Scalability Needs:
Thoroughly analyze your client’s current and future usage patterns to determine anticipated growth and scalability requirements.
Modular Design:
Develop software using a modular architecture with well-defined components that can be scaled independently. This enables easier maintenance and future enhancements.
Choose the Right Technologies:
Select technologies known for their scalability, such as cloud-based solutions and distributed databases.
Performance Optimization:
Optimize the software code for efficiency to ensure smooth performance even under increased load. Load testing can help identify and address potential performance bottlenecks.
Monitoring & Alerting:
Implement comprehensive monitoring tools to track system performance and resource utilization. Set up alerts to identify any potential scalability issues proactively.
The Benefits of Building Secure and Scalable Software
By prioritizing both security and scalability, IT firms can deliver significant benefits to their clients:
Enhanced Security Posture:
Secure software development practices minimize the risk of data breaches and cyberattacks, safeguarding client data and protecting their brand reputation.
Improved User Experience:
Scalable software ensures smooth performance and responsiveness even under increasing user loads. This translates to a positive user experience, fostering client satisfaction and loyalty.
Reduced Long-Term Costs:
Investing in security and scalability upfront can save significant costs in the long run. Addressing security vulnerabilities after deployment is often more expensive and time-consuming.
Increased Business Agility:
Scalable software allows clients to adapt their IT infrastructure to accommodate evolving business needs, propelling them towards greater agility and competitiveness.
Competitive Advantage:
In today’s landscape, secure and scalable software solutions are a differentiator. IT firms that prioritize these aspects can gain a competitive edge and attract new clients.
Collaboration is Key: Building a Culture of Security and Scalability
Building secure and scalable software requires a collaborative effort within the IT firm:
Executive Sponsorship:
Leadership buy-in for security and scalability initiatives is crucial for allocating resources and ensuring successful implementation.
Security Champions:
Designate security champions within the development team to promote security awareness and best practices.
DevOps Collaboration:
Foster close collaboration between developers and IT operations teams (DevOps) to ensure seamless integration of security and scalability considerations throughout the development and deployment process.

Conclusion: Building a Secure and Scalable Future
In the ever-evolving IT landscape, secure and scalable software development is no longer a luxury; it’s a necessity. By adopting secure coding practices, implementing robust security measures, and prioritizing scalability from the outset, IT firms can empower their clients to thrive in the digital age.
Now, let’s explore additional considerations for IT firms, delve into the role of DevOps in security and scalability, and examine emerging trends in secure and scalable software development.
Additional Considerations for Building Secure and Scalable Software
Third-Party Software Integration:
When integrating third-party libraries or software components, thoroughly assess their security posture and ensure they align with your overall security requirements.
Version Control & Patch Management:
Implement a robust version control system to track code changes and facilitate rollbacks if necessary. Establish a systematic approach to patch management to address security vulnerabilities promptly.
Incident Response Planning:
Develop a comprehensive incident response plan to define how your team will react to security breaches or potential vulnerabilities. This plan should outline communication protocols, mitigation strategies, and recovery procedures.
Disaster Recovery Planning:
In addition to security breaches, unforeseen events like hardware failures or natural disasters can disrupt operations. Create a disaster recovery plan to ensure business continuity and minimize downtime in such scenarios.
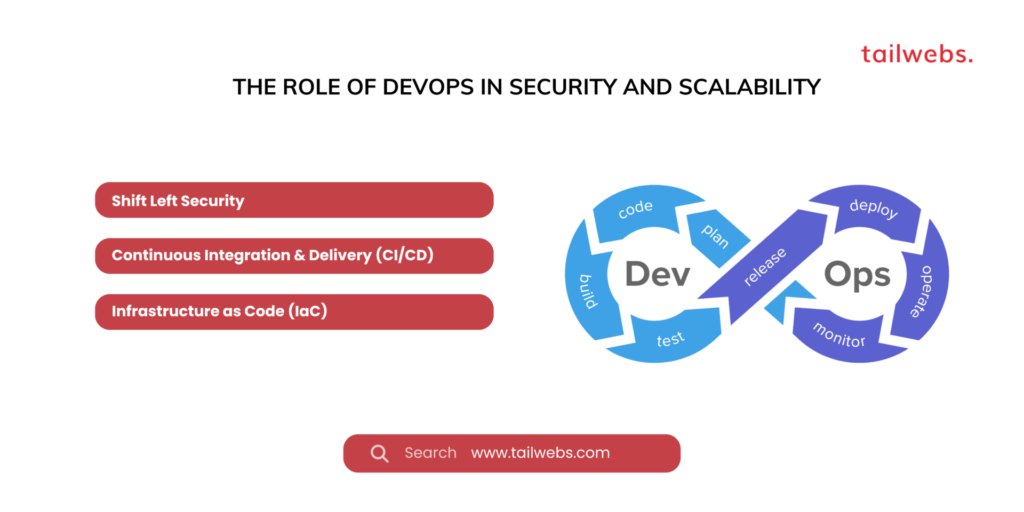
The Role of DevOps in Security and Scalability
DevOps practices bridge the gap between development and operations teams, fostering collaboration and streamlining software delivery. Here’s how DevOps contributes to secure and scalable software:
Shift Left Security:
By integrating security considerations earlier in the development lifecycle (DevSecOps), vulnerabilities can be identified and addressed earlier, reducing the risk of security flaws persisting into production.
Continuous Integration & Delivery (CI/CD):
Automated CI/CD pipelines enable frequent and secure deployments, facilitating faster feedback loops and ensuring consistency between development, testing, and production environments.
Infrastructure as Code (IaC):
IaC tools automate infrastructure provisioning and configuration, promoting consistency and repeatability. This can be crucial for scaling infrastructure efficiently and securely.
Emerging Trends in Secure and Scalable Software Development
The landscape of secure and scalable software development is constantly evolving. Here are some key trends to watch:
Security Automation:
The rise of security automation tools allows for automated vulnerability scanning, code analysis, and security configuration management, streamlining security practices and reducing human error.
Containerization & Serverless Computing:
Containerized applications and serverless architectures offer benefits for scalability and security. Microservices architecture, where applications are broken down into smaller, independent services, can also enhance scalability and security.
API Security:
As APIs become ubiquitous, securing APIs to prevent unauthorized access and data breaches is paramount.
Security Orchestration, Automation, and Response (SOAR):
SOAR platforms can automate routine security tasks, freeing up security professionals to focus on more complex threats.
Artificial Intelligence (AI) in Security:
AI-powered solutions are increasingly used to detect anomalies, identify potential security threats, and automate security incident response.
Conclusion: Building a Culture of Security and Scalability
By prioritizing secure and scalable software development practices, IT firms can deliver long-term value to their clients. Building a culture of security within the organization, fostering collaboration between development and operations teams, and embracing emerging trends are crucial for success in today’s dynamic IT landscape.
Remember, security and scalability are not one-time achievements but ongoing processes. By continuously adapting to new technologies, staying informed about emerging threats, and prioritizing both security and scalability throughout the software development lifecycle, IT firms can empower their clients to build a secure and scalable digital future.